Accessing your Raspberry Pi remotely via SSH can be a game-changer, especially when you're working behind a firewall and don't have access to a Windows machine. Whether you're a hobbyist, a developer, or someone managing IoT devices, understanding how to bypass these restrictions is essential. This guide will walk you through the process step-by-step, ensuring you can securely connect to your Raspberry Pi without relying on proprietary software or expensive tools. With the right techniques, you can achieve seamless remote access, even in restrictive network environments.
Remote access to your Raspberry Pi can unlock a world of possibilities, from managing smart home devices to deploying server applications. However, firewalls and the absence of a Windows machine can pose significant challenges. This article dives deep into the methods and tools that allow you to overcome these barriers. By leveraging free, open-source solutions and adhering to best practices, you’ll be able to connect to your Pi without compromising security or spending a dime.
In today’s interconnected world, the ability to access devices remotely is more important than ever. Whether you're troubleshooting issues, deploying updates, or simply monitoring your projects, knowing how to connect to your Raspberry Pi securely is invaluable. In the sections that follow, we’ll explore various techniques, tools, and tips to ensure you can access your Raspberry Pi via SSH behind a firewall without Windows, all for free. Let’s get started!
Read also:Understanding The Controversy Around The Pajeet Slur Origins Impact And Modern Usage
Table of Contents
- Why Use SSH for Raspberry Pi Access?
- How Can You Set Up SSH on Your Raspberry Pi?
- What Are the Challenges of Accessing Raspberry Pi Behind a Firewall?
- How to Access Raspberry Pi via SSH Without Windows?
- What Tools Can You Use for Free SSH Access?
- How to Secure Your SSH Connection?
- Troubleshooting Common SSH Issues
- Frequently Asked Questions
Why Use SSH for Raspberry Pi Access?
SSH, or Secure Shell, is a protocol that allows you to securely connect to and manage remote devices, such as your Raspberry Pi. Unlike other methods, SSH encrypts all communication between your local machine and the remote device, ensuring that sensitive data remains protected. This is especially important when accessing your Raspberry Pi over public or untrusted networks, where data interception is a real risk.
Besides security, SSH offers unparalleled flexibility. It allows you to execute commands, transfer files, and even run graphical applications on your Raspberry Pi from virtually anywhere. For developers and hobbyists, this means you can work on your projects without needing physical access to the device. Additionally, SSH is platform-independent, meaning you can use it on Linux, macOS, and even Windows (though this guide focuses on free, non-Windows methods).
Another advantage of SSH is its lightweight nature. Unlike GUI-based remote access tools, SSH consumes minimal bandwidth and system resources, making it ideal for low-power devices like the Raspberry Pi. Whether you're managing a single Pi or an entire network of devices, SSH provides a reliable and efficient way to stay connected.
How Can You Set Up SSH on Your Raspberry Pi?
Enabling SSH on Raspberry Pi
To access your Raspberry Pi via SSH, you first need to enable the SSH service. By default, SSH is disabled on most Raspberry Pi distributions for security reasons. However, enabling it is a straightforward process. Start by connecting your Pi to a monitor and keyboard, or access it via a local network connection.
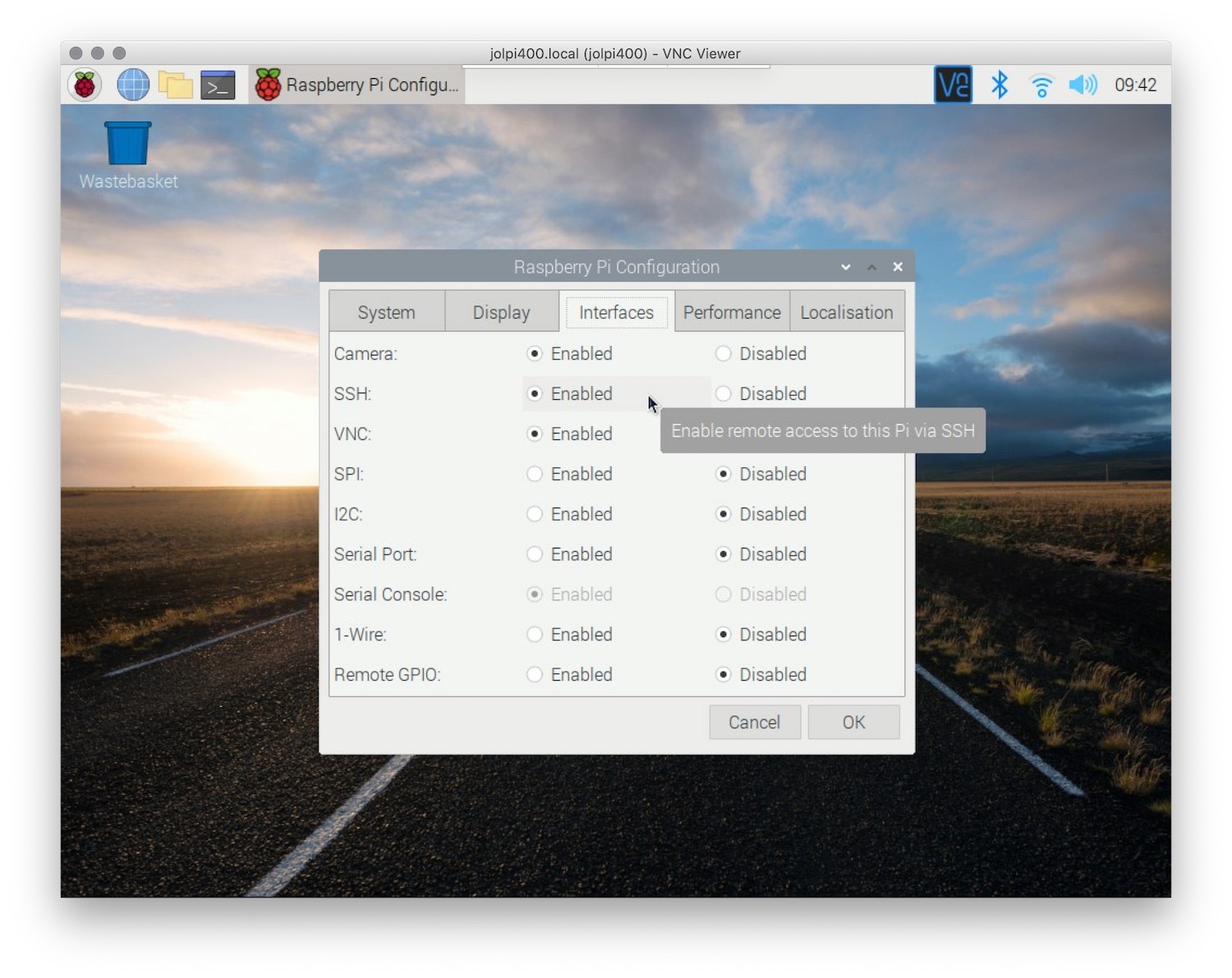
If you're using the Raspberry Pi OS, navigate to the "Preferences" menu and select "Raspberry Pi Configuration." Under the "Interfaces" tab, enable SSH. Alternatively, you can create an empty file named "ssh" (without any extension) in the boot partition of your SD card. This method is particularly useful if you’re setting up the Pi headlessly (without a monitor).
Once SSH is enabled, ensure your Raspberry Pi is connected to the same network as your local machine. You can find the Pi's IP address by running the hostname -I command in the terminal. With SSH enabled and the IP address in hand, you're ready to connect remotely.
Read also:Who Are Nick Cannon Parents A Deep Dive Into Their Influence And Legacy
Configuring SSH Keys for Security
While password-based authentication is convenient, it’s not the most secure method for SSH access. Instead, consider using SSH keys, which provide a higher level of security. SSH keys consist of a public key (stored on the Raspberry Pi) and a private key (stored on your local machine).
To generate an SSH key pair, use the ssh-keygen command on your local machine. This will create two files: id_rsa (private key) and id_rsa.pub (public key). Copy the public key to your Raspberry Pi by running ssh-copy-id pi@. Once the key is added, you can disable password authentication in the SSH configuration file (/etc/ssh/sshd_config) for added security.
What Are the Challenges of Accessing Raspberry Pi Behind a Firewall?
Understanding Firewall Restrictions
Firewalls are designed to protect networks by blocking unauthorized access. While this is essential for security, it can also prevent legitimate connections, such as SSH access to your Raspberry Pi. Firewalls typically block incoming connections on specific ports, including the default SSH port (22).
In many cases, network administrators configure firewalls to allow only outgoing connections. This means your Raspberry Pi can initiate connections to external servers, but external devices cannot connect to it. To overcome this, you’ll need to use techniques like port forwarding, reverse SSH tunnels, or third-party services that bypass these restrictions.
How to Bypass Firewall Restrictions?
One effective way to bypass firewall restrictions is by using a reverse SSH tunnel. This involves setting up your Raspberry Pi to initiate a connection to an external server, which then forwards incoming SSH requests back to the Pi. Tools like autossh can help maintain persistent connections, ensuring your Pi remains accessible even if the connection drops.
Another option is to use a third-party service like ngrok or PageKite. These services create secure tunnels to your Raspberry Pi, bypassing firewall restrictions without requiring complex configurations. While some features may require a paid subscription, the free tiers are often sufficient for personal use.
How to Access Raspberry Pi via SSH Without Windows?
If you don’t have access to a Windows machine, don’t worry—there are plenty of free tools available for Linux and macOS users. On Linux, you can use the built-in terminal to connect to your Raspberry Pi via SSH. Simply run ssh pi@, replacing
For macOS users, the process is similar. Open the Terminal app and use the same ssh command. Both operating systems come with SSH pre-installed, so there’s no need to download additional software. If you prefer a graphical interface, tools like PuTTY for Linux or Termius for macOS offer user-friendly alternatives.
What Tools Can You Use for Free SSH Access?
Several free tools can simplify SSH access to your Raspberry Pi. For example, OpenSSH is a widely-used, open-source implementation of the SSH protocol. It’s available on most Linux distributions and macOS, making it an excellent choice for non-Windows users.
Other tools like MobaXterm (for Linux) and Cyberduck (for macOS) provide additional features, such as file transfer capabilities and graphical interfaces. These tools are particularly useful if you’re managing multiple devices or need to transfer files frequently.
How to Secure Your SSH Connection?
Securing your SSH connection is crucial, especially when accessing your Raspberry Pi remotely. Start by changing the default username and password. The default username for Raspberry Pi is "pi," which is well-known and often targeted by attackers.
Next, consider changing the default SSH port (22) to a non-standard port. This won’t make your connection invulnerable, but it can reduce the likelihood of automated attacks. Additionally, disable root login and use strong, complex passwords or SSH keys for authentication.
Troubleshooting Common SSH Issues
Even with careful setup, you may encounter issues when connecting to your Raspberry Pi via SSH. Common problems include connection timeouts, authentication failures, and permission errors. To troubleshoot, start by verifying that SSH is enabled on your Pi and that the correct IP address is being used.
If you’re still unable to connect, check your firewall settings and ensure the SSH port is open. You can also review the SSH logs on your Raspberry Pi (/var/log/auth.log) for more information. Finally, ensure your local machine’s SSH client is configured correctly and that any required keys or credentials are in place.
Frequently Asked Questions
Can I Access My Raspberry Pi via SSH Without an Internet Connection?
Yes, you can access your Raspberry Pi via SSH on a local network without an internet connection. Simply ensure both devices are connected to the same network and use the Pi’s local IP address.
Is It Safe to Use Third-Party Services for SSH Access?
While third-party services like ngrok and PageKite are generally safe, it’s important to use trusted providers and review their privacy policies. Always enable encryption and avoid transmitting sensitive data over unsecured connections.
What Should I Do If My SSH Connection Keeps Dropping?
If your SSH connection keeps dropping, consider using autossh to maintain a persistent connection. Additionally, check your network stability and ensure the Pi’s power supply is adequate.
Learn more about SSH on Raspberry Pi.
In conclusion, accessing your Raspberry Pi via SSH behind a firewall without Windows is entirely possible with the right tools and techniques. By following the steps outlined in this guide, you can achieve secure, reliable remote access to your Pi, unlocking its full potential for your projects and applications.