Cybercriminals are constantly seeking ways to exploit vulnerabilities in IoT devices, making robust security measures more critical than ever. One such measure gaining traction is the IoT secure tunnel, a technology designed to create encrypted pathways for secure communication between devices and servers. This innovation ensures that sensitive data remains protected from prying eyes while enabling seamless connectivity across networks. Without such safeguards, businesses and individuals alike face the risk of data breaches, financial losses, and reputational damage. IoT secure tunnels are not just about encryption; they represent a holistic approach to securing data transmission. By isolating communication channels and encrypting data packets, these tunnels prevent unauthorized access and man-in-the-middle attacks. For industries like healthcare, manufacturing, and transportation, where real-time data exchange is crucial, IoT secure tunnels provide a reliable way to maintain operational integrity. They also support compliance with data protection regulations like GDPR and HIPAA, ensuring organizations meet legal standards while safeguarding their digital ecosystems. As the IoT landscape continues to expand, the importance of secure communication cannot be overstated. With billions of devices expected to be connected globally by 2030, the need for scalable and secure solutions like IoT secure tunnels is more pressing than ever. These tunnels not only protect data but also enhance user trust, making them a cornerstone of modern IoT infrastructure. Understanding how IoT secure tunnels work and their benefits can empower businesses and individuals to adopt smarter, safer practices in their digital interactions.
Table of Contents
- What Is an IoT Secure Tunnel?
- How Does an IoT Secure Tunnel Work?
- Why Is an IoT Secure Tunnel Important for Your Business?
- What Are the Benefits of Using an IoT Secure Tunnel?
- How Can You Implement an IoT Secure Tunnel in Your Network?
- What Are the Common Challenges with IoT Secure Tunnels?
- How Does IoT Secure Tunnel Compare to Other Security Solutions?
- Frequently Asked Questions About IoT Secure Tunnels
What Is an IoT Secure Tunnel?
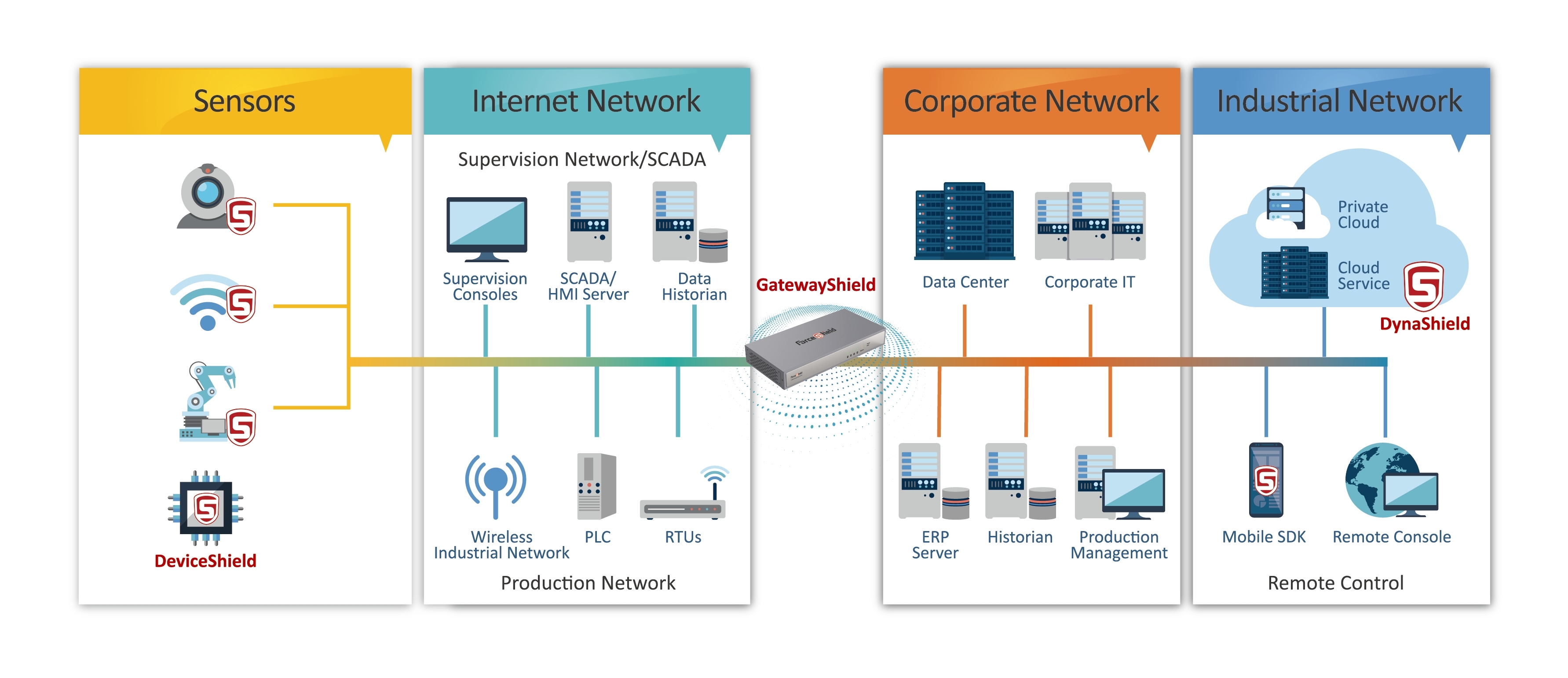
At its core, an IoT secure tunnel is a virtual, encrypted pathway that facilitates secure communication between IoT devices and cloud servers or other endpoints. Think of it as a protective shield around your data, ensuring that only authorized entities can access or interpret it. This technology is built on principles of cryptography, where data is transformed into unreadable formats during transmission and decrypted only by the intended recipient. The result is a secure channel that prevents unauthorized access, eavesdropping, and tampering. There are several types of IoT secure tunnels, each tailored to specific use cases and requirements. For instance, some tunnels are designed for lightweight devices with limited computational power, such as smart sensors or wearables. These tunnels use lightweight encryption protocols to minimize resource consumption while maintaining security. On the other hand, enterprise-grade IoT secure tunnels cater to high-stakes environments like industrial IoT (IIoT) or smart cities, where large volumes of data need to be transmitted securely in real-time. These tunnels often employ advanced encryption standards (AES) and Transport Layer Security (TLS) protocols to ensure robust protection. Another distinction lies in the deployment models of IoT secure tunnels. Some tunnels operate as part of a broader IoT platform, offering integrated security features alongside device management and analytics tools. Others function as standalone solutions, allowing businesses to customize their security architecture based on specific needs. Regardless of the type, all IoT secure tunnels share a common goal: to create a secure, reliable, and efficient communication channel that safeguards sensitive data from cyber threats.
How Does an IoT Secure Tunnel Work?
To understand how an IoT secure tunnel operates, it’s essential to break down the process into its key components and steps. At the heart of this technology lies encryption, a process that converts plain text data into ciphertext using algorithms and cryptographic keys. This ensures that even if data is intercepted during transmission, it remains unintelligible to unauthorized parties. Encryption protocols like TLS and Secure Sockets Layer (SSL) play a pivotal role in establishing secure connections between devices and servers. The process begins when an IoT device initiates a connection request to a server or cloud platform. During this handshake phase, both parties exchange cryptographic keys to establish a secure session. Once the keys are verified, the IoT secure tunnel is established, and data transmission begins. The tunnel acts as a protective layer, encapsulating data packets and encrypting them before sending them across the network. On the receiving end, the server decrypts the data using the shared keys, ensuring that only the intended recipient can access the information.
Read also:Who Is Sean John Discovering The Legacy Of A Fashion Icon
What Are the Key Components of an IoT Secure Tunnel?
Several components work together to make an IoT secure tunnel function effectively. First, there’s the authentication mechanism, which verifies the identity of both the device and the server. This step is crucial to prevent unauthorized devices from accessing the network. Next, the encryption engine applies cryptographic algorithms to secure data packets, ensuring confidentiality and integrity. Finally, the tunneling protocol manages the encapsulation and transmission of data, often leveraging technologies like IPsec (Internet Protocol Security) or GRE (Generic Routing Encapsulation) to create the secure pathway.
Why Is Encryption Critical in IoT Secure Tunnels?
Encryption is the backbone of IoT secure tunnels, as it ensures that data remains private and tamper-proof during transmission. Without encryption, sensitive information like user credentials, financial data, or operational metrics could be intercepted and exploited by cybercriminals. By encrypting data, IoT secure tunnels not only protect privacy but also enhance trust and reliability in IoT ecosystems.
Why Is an IoT Secure Tunnel Important for Your Business?
In today’s digital-first economy, businesses rely heavily on IoT devices to streamline operations, improve efficiency, and deliver better customer experiences. However, this reliance also exposes organizations to significant security risks. Cyberattacks targeting IoT devices have surged in recent years, with hackers exploiting weak points in networks to steal data, disrupt services, and even cause physical damage. This is where IoT secure tunnels come into play, offering a proactive defense mechanism to safeguard business operations. One of the primary reasons IoT secure tunnels are indispensable for businesses is their ability to protect sensitive data. For example, in the healthcare sector, IoT devices like patient monitors and wearable health trackers collect and transmit critical health information. An IoT secure tunnel ensures that this data remains confidential and tamper-proof, meeting regulatory requirements like HIPAA. Similarly, in the financial industry, secure tunnels protect transactions and customer data from unauthorized access, reducing the risk of fraud and identity theft. Another key benefit is the enhancement of operational resilience. By securing communication channels, IoT secure tunnels prevent disruptions caused by cyberattacks, ensuring that devices and systems continue to function smoothly. This is particularly important for industries like manufacturing, where downtime can result in significant financial losses. Additionally, IoT secure tunnels support remote device management, enabling businesses to monitor and update devices securely, even from distant locations.
What Are the Benefits of Using an IoT Secure Tunnel?
The advantages of implementing an IoT secure tunnel extend beyond just security. One major benefit is improved scalability. As businesses expand their IoT ecosystems, secure tunnels provide a consistent and reliable way to manage growing volumes of data and devices. This scalability ensures that security measures remain effective, regardless of the size or complexity of the network. Another benefit is cost efficiency. By preventing data breaches and minimizing downtime, IoT secure tunnels help businesses avoid the financial repercussions of cyberattacks. They also reduce the need for costly post-attack recovery efforts, such as forensic investigations and regulatory fines. Furthermore, secure tunnels enhance user trust, which is invaluable for customer retention and brand reputation.
How Can You Implement an IoT Secure Tunnel in Your Network?
Implementing an IoT secure tunnel involves several steps, starting with a thorough assessment of your network architecture and security requirements. Begin by identifying the devices and endpoints that need protection, as well as the types of data they transmit. This will help you choose the right tunneling protocol and encryption standards for your needs. For example, lightweight devices may require protocols like DTLS (Datagram Transport Layer Security), while enterprise-grade systems might benefit from IPsec. Next, select a reliable IoT platform or standalone solution that supports secure tunneling. Many cloud providers offer built-in tunneling capabilities, making it easier to integrate secure tunnels into your existing infrastructure. Once the solution is in place, configure the authentication and encryption settings to ensure maximum security. Regularly update these settings to address emerging threats and vulnerabilities.
What Are the Common Challenges with IoT Secure Tunnels?
Despite their advantages, IoT secure tunnels are not without challenges. One common issue is compatibility, as not all devices support advanced encryption protocols. This can create gaps in security, especially in heterogeneous IoT environments. Another challenge is the computational overhead associated with encryption, which can strain resource-constrained devices.
Read also:Nurdian Cuaca Exploring The Life And Legacy Of A Remarkable Figure
How Does IoT Secure Tunnel Compare to Other Security Solutions?
When compared to traditional firewalls or intrusion detection systems, IoT secure tunnels offer a more targeted approach to securing data transmission. While firewalls focus on blocking unauthorized access at the network perimeter, secure tunnels protect data in transit, ensuring end-to-end security. This makes them a complementary solution rather than a replacement for existing measures.
Frequently Asked Questions About IoT Secure Tunnels
What Are the Key Features of an IoT Secure Tunnel?
An IoT secure tunnel typically includes features like end-to-end encryption, authentication mechanisms, and support for multiple tunneling protocols.
How Can IoT Secure Tunnels Prevent Cyberattacks?
By encrypting data and isolating communication channels, IoT secure tunnels prevent unauthorized access and man-in-the-middle attacks.
Are IoT Secure Tunnels Suitable for Small Businesses?
Yes, IoT secure tunnels are scalable and can be tailored to meet the needs of small businesses, offering cost-effective security solutions.
For more information on IoT security, you can explore resources like the IoT Security Foundation.